Quality Standards for Padlocks
-
Key System Selection
>Identifiability: Safety devices must be identifiable.
Purpose: Safety devices should only be used for energy control and not for other purposes.
Principle Compliance: Adhere strictly to the "One Employee - One Lock - One Key" principle. Each individual should only have their own key, clearly defining responsibility.
Product Requirements: Products should meet the requirements of durability, standardization, robustness, and identifiability.
-
Safety Padlock Marking
>Safety Padlock Marking: Critical Standards for Industrial Compliance
Engineered to meet OSHA, ANSI, and ISO requirements, safety padlock marking ensures clear identification, accountability, and risk mitigation in high-hazard environments. -
Material of Safety Padlocks
>1. Core Materials for Safety Padlocks
1.1 Stainless Steel
- Grade 304:
- Properties: High corrosion resistance, rust-proof, and durable in indoor/outdoor environments.
- Applications: Pharmaceutical storage, food processing, and chemical plants .
- Standards: Compliant with FDA and USDA regulations for food-contact surfaces .
- Grade 316:
- Properties: Contains molybdenum for enhanced resistance to saltwater and acidic conditions.
- Applications: Maritime facilities, offshore platforms, and coastal regions .
- Case Study: A maritime logistics company reduced lock replacement costs by 40% using 316 stainless steel padlocks in saltwater environments .
1.2 Alloy Steel
- Boron Alloy:
- Properties: High tensile strength (≥1124 lb) and resistance to physical attacks (e.g., cutting, drilling) .
- Applications: Critical infrastructure (e.g., power plants, oil refineries) and high-security storage .
- Laminated Steel:
- Properties: Multi-layered construction resists sawing and forced entry.
- Standards: Meets ANSI Grade 1 requirements for commercial security .
1.3 Aluminum
- Anodized Aluminum:
- Properties: Lightweight, corrosion-resistant, and UV-stable.
- Applications: Construction sites, temporary fencing, and outdoor equipment storage .
- Certifications: Compliant with EN 12320 for outdoor durability .
1.4 Nylon & Composite Materials
- Nylon:
- Properties: Non-conductive, non-sparking, and lightweight.
- Applications: Electrical lockout, hospitals, and mines .
- Safety Feature: Resists electrostatic discharge (ESD) in sensitive environments .
- Composite Polymers (e.g., Xenoy®):
- Properties: Impact-resistant, chemical-resistant, and temperature-stable (-40°F to 140°F) .
- Applications: Pharmaceutical cleanrooms and chemical processing plants .
1.5 Copper Alloy
- Brass:
- Properties: Non-magnetic and corrosion-resistant.
- Applications: Electronics manufacturing and MRI facilities .
- Bronze:
- Properties: High conductivity and resistance to biofouling.
- Applications: Water treatment plants and marine environments .
- Grade 304:
-
Key Coding
>Key Coding: Precision Engineering for Industrial Access Control
Engineered to ensure traceability, security, and compliance, key coding systems are the backbone of modern lockout/tagout (LOTO) and high-security applications.1. Core Principles of Key Coding
Key coding assigns unique identifiers to keys, enabling hierarchical access control and auditability. Critical components include:- Mechanical Coding:
- Bitting Patterns: Laser-engraved cuts or depressions on key blades that correspond to lock tumblers .
- Key Blanks: Restricted blanks (e.g., Abloy® or Medeco®) prevent unauthorized duplication .
- Digital Integration:
- RFID Tags: Encrypted chips store key ID and access permissions for real-time tracking .
- QR Codes: Link to digital lockout procedures or maintenance logs .
- Mechanical Coding:
-
OSHA Lockout Device Standards
>OSHA Lockout Device Standards: Compliance, Design, and Best Practices
Engineered to mitigate workplace hazards, OSHA lockout device standards ensure the safe control of hazardous energy during maintenance, repair, or servicing activities. This guide outlines the technical requirements, compliance frameworks, and industry applications of lockout/tagout (LOTO) devices, aligned with 29 CFR 1910.147 and ANSI/ASSP Z244.1-2024.1. Core Requirements for OSHA-Compliant Lockout Devices
OSHA’s 29 CFR 1910.147 mandates lockout devices to:- Be Durable: Resist environmental degradation (e.g., corrosion, UV exposure) and physical tampering .
- Be Standardized: Use uniform color, shape, or size within a facility; tags must follow standardized print and format .
- Be Substantial: Prevent unauthorized removal without specialized tools (e.g., bolt cutters) .
- Identify Users: Display the name or ID of the authorized employee who applied the device .
- Warn Against Hazards: Include clear legends like “DO NOT START” or “DO NOT ENERGIZE” .
Key Exceptions:- Tagout Devices: Permitted only if they provide equivalent safety to locks (e.g., non-reusable nylon cable ties with ≥50 lb breaking strength) .
- Group Lockout Systems: Require a centralized lockbox for multi-worker scenarios, ensuring all personnel remove their locks before re-energization .
-

Colors visually distinguish and standardize lockout padlocks within your facility.
-

Shackle height and material options available for common lockout applications.
KEY SYSTEMKey Systems and Selection Methods
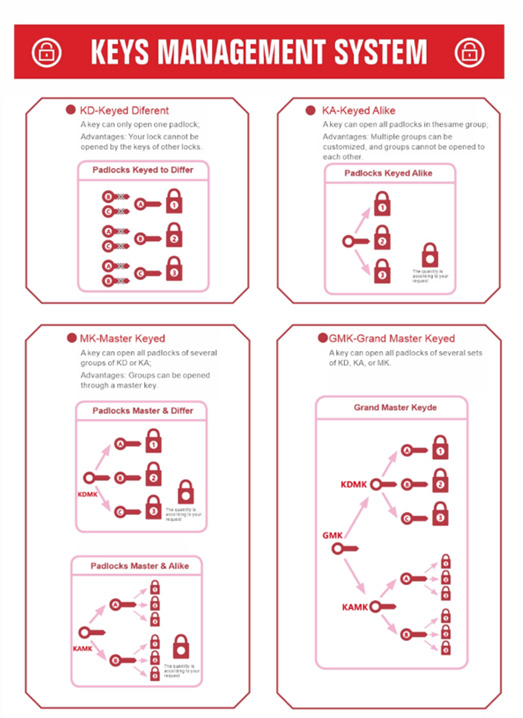
Key Systems and Selection Methods
Selecting the appropriate key system for your padlocks is essential to ensuring security, convenience, and effective management. Here’s an overview of the different key systems and how to choose the right one for your needs:
-
Keyed Different (KD)
>KD Keyed Different represents a robust, secure key system where each key is uniquely matched to one padlock. Specifically, one key operates only its corresponding padlock, with no cross - functionality. The core advantage is its exceptional security—no other padlock’s key can unlock a specific padlock, drastically reducing unauthorized access risks. This system is perfect for scenarios demanding high - level security and individualization, ensuring each padlock remains safeguarded by the exclusivity of its key.
-
Keyed Alike (KA)
>KA Keyed Alike is a specialized key system where a single key efficiently unlocks all padlocks within its designated group. This system excels in customization, allowing for the creation of multiple KA groups. Each group operates independently—while one key seamlessly accesses all padlocks in its own group, there is no inter - group operability, enhancing security and organization. The number of padlocks in each group can be tailored to specific needs, offering flexibility for diverse applications. Whether for commercial, residential, or industrial use, KA Keyed Alike balances convenience with controlled access, ensuring each group functions autonomously while meeting unique requirements.
-
Grand Master Keyed(GMK)
>The GMK (Grand Master Keyed) system exemplifies advanced hierarchical key - management, delivering unmatched versatility and control. A single Grand Master Key (GMK) is engineered to unlock all padlocks across multiple groups—KD (Keyed Different), KA (Keyed Alike), and MK (Master Keyed). This system is pivotal for complex security ecosystems where centralized access control is paramount. Its strength lies in offering overarching access while preserving each group’s integrity. Whether overseeing diverse facilities or intricate setups, GMK ensures operational efficiency without sacrificing security. Padlock quantities can be customized to specific needs, enhancing adaptability. This sophisticated architecture merges convenience and security, providing a robust solution for high - level access - control demands.
-
MK Master Keyed
>The MK (Master Keyed) system offers a sophisticated access - control solution. In this architecture, individual keys (e.g., Key A, B, or C) each operate a specific padlock (1, 2, 3), while a master key provides overarching access to these padlocks, ensuring centralized management.For KDMK and KAMK, a single key can unlock all padlocks across multiple KD groups. This design grants dual - layer convenience: regular keys manage specific padlocks, while the master key offers oversight. The advantage lies in centralized control—padlocks within KD groups are accessible via the master key, streamlining operations. Ideal for environments requiring structured yet flexible access, this system adapts to varying needs, with padlock quantities customizable as required. It harmonizes security and convenience, allowing efficient management while maintaining robust protection.
-
SELECTION METHOD
-
Step 1
Assess the Security Requirement
High Security: Opt for Keyed Different or Master Keyed systems.
Moderate Security with Convenience: Keyed Alike systems.
-
Step 2
Determine the Number of Users and Access Levels
Single User/Single Point: Keyed Different.
Multiple Users/Multiple Points: Keyed Alike or Master Keyed.
-
Step 3
Consider the Management and Maintenance
Ease of Management: Keyed Alike systems reduce the number of keys to manage.
Supervisor Access: Master Keyed systems allow supervisors to access all locks when needed.
-
Step 4
Evaluate the Environment
High Frequency Use: Durable and easy-to-use systems like Keyed Alike.
Complex Environments: Master Keyed systems for better control and emergency access.
-
Step 5
Plan for Future Expansion
Scalability: Ensure the chosen key system can be expanded as needed without compromising security or convenience.
EXAMPLES OF SELECTION
Single Employee Managing Multiple Locks:
Keyed Alike: The employee uses one key to access all their assigned locks.
Multiple Employees with Supervisor Access:
Master Keyed: Each employee has a unique key for their lock, and the supervisor has a master key to access all locks.
High-Security Areas with Individual Access Control:
Keyed Alike Master Keyed: Each department has its own set of keyed alike locks, and a master key provides access across departments.
Facilities with Different Departments:
Keyed Alike Master Keyed: Each department has its own set of keyed alike locks, and a master key provides access across departments.
By carefully considering these factors and following the selection method, you can choose the most suitable key system to meet your security and operational needs.
KEYING OPTIONS
- Key Coding Registration
- Laser printing
- Maintenance of Safety Padlocks
- Product Quality Commitment Letter
- Custom Safety Tags
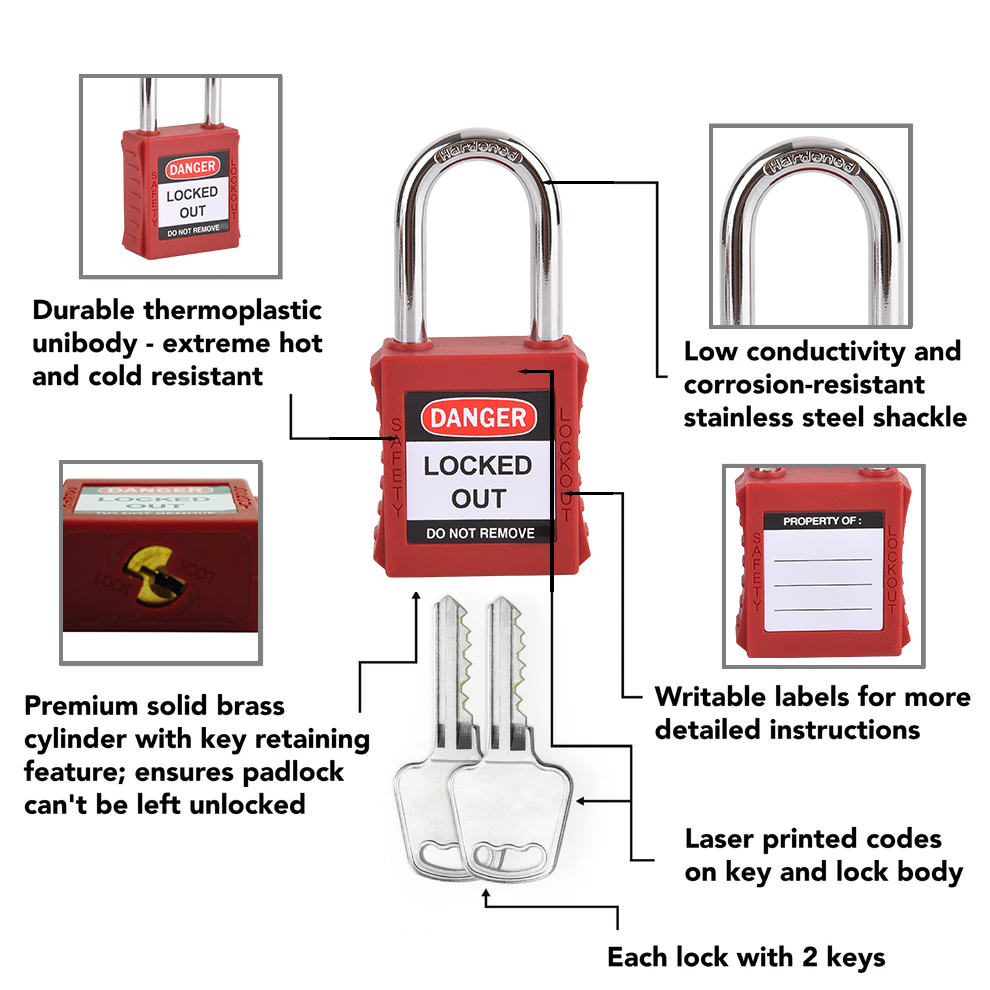
Key Coding Registration
Safety Padlock Key Coding RegistrationKey Coding Registration for safety padlocks is a systematic pr
Conclusion
Key Coding Registration is a foundational element of safety padlock management, merging administrative rigor with technological precision to enforce LOTO compliance, prevent unauthorized equipment operation, and maintain a culture of accountability. By systematically linking keys to users, assets, and safety protocols, organizations mitigate risks, streamline audits, and ensure that energy-control measures remain effective and traceable in high-hazard work environments.
This description emphasizes regulatory alignment, operational efficiency, and security, using industry-standard terminology to address the needs of safety professionals, compliance officers, and industrial asset managers.

Laser printing
Laser Printing on Safety PadlocksLaser printing is a precision technology used to apply permanent, h
Technical Advantages
- Permanent Marking: Laser etching creates indelible marks by altering the surface material (e.g., metal oxidation, polymer discoloration), resisting wear from abrasion, chemicals, UV exposure, or extreme temperatures—ideal for harsh industrial environments.
- High Precision: Uses advanced laser systems (e.g., fiber, CO₂) to achieve sharp, consistent text (0.5mm+ height) and intricate symbols (e.g., ANSI safety icons, GHS hazard pictograms) with minimal distortion.
- Material Compatibility: Effective on diverse padlock materials, including:
- Stainless steel, alloy steel, or brass (via color-changing oxidation or surface etching).
- Powder-coated, zinc-plated, or polymer-coated surfaces (ablating coatings to reveal underlying material).
- Nylon or plastic components (for non-metallic safety padlocks).
Key Marking Elements
- Identifiers:
- Unique serial numbers, asset tags, or employee/team IDs for traceability in LOTO procedures.
- Facility-specific codes or lockout station references to streamline equipment isolation.
- Safety Information:
- Regulatory compliance logos (e.g., OSHA, CE, ANSI Z359).
- Warning messages (e.g., "DO NOT REMOVE WITHOUT AUTHORIZATION") or instructional text.
- Standardized symbols (e.g., padlock-and-key icon, hazard warning triangles) for quick visual recognition.
- Custom Graphics:
- Company logos or brand identifiers for asset management.
- Color-coded zones (via laser-induced color contrast) to denote hazard levels (e.g., red for high-risk, yellow for caution).
Compliance & Performance
- Regulatory Alignment: Meets global standards for safety signage (ANSI Z535.4, ISO 7010) and LOTO documentation (OSHA 1910.147), ensuring markings remain clear throughout the padlock’s lifecycle.
- Environmental Resistance:
- Chemical Proof: Marks withstand exposure to oils, solvents, and cleaning agents (tested per ASTM D543).
- Weatherproof: UV-stable markings retain visibility in outdoor or sun-exposed environments (no fading for 5+ years per ISO 4892-2).
- High/Low Temp Tolerance: Functional from -40°C to 200°C, suitable for extreme industrial conditions (e.g., refineries, freezers).
Process Efficiency
- Customization Flexibility: Digital design tools allow quick adaptation of text, symbols, or layouts to meet unique client or project requirements.
- Non-Contact Technology: Eliminates physical wear on padlock surfaces (no stamping or engraving-induced stress points), preserving structural integrity.
- Traceability Integration: Enables QR codes or Data Matrix codes for digital LOTO record-keeping, linking padlock usage to maintenance logs or incident reports.
Industry Applications
- Manufacturing & Industrial: Marking equipment-specific padlocks for LOTO compliance, ensuring clear identification during machine shutdowns.
- Chemical & Petrochemical: Durable hazard warnings on padlocks securing hazardous material storage or processing units.
- Energy & Utilities: Asset tagging for padlocks used in electrical, hydraulic, or thermal isolation, withstanding harsh operational environments.
- Construction & Logistics: High-visibility markings for temporary lockout devices on mobile equipment or shared tools.
Quality Assurance
- Post-Processing Inspection: Automated vision systems verify mark clarity, alignment, and compliance with design specifications.
- Adhesion Testing: For coated surfaces, cross-cut tests (ASTM D3359) ensure laser-ablated areas maintain substrate integrity.

Maintenance of Safety Padlocks
Maintenance of Safety PadlocksSafety padlocks are critical components of lockout/tagout (LOTO) proce
1. Regular Inspections
- Visual Checks: Inspect for physical damage (e.g., cracks, bent shackles, corroded components) or wear on the body, shackle, locking mechanism, and safety labels.
- Functionality Testing: Verify smooth operation of the locking/unlocking mechanism:
- Ensure the shackle moves freely without binding and engages fully when locked.
- Test key insertion/removal to confirm proper alignment and no key breakage risks.
- For serialized or numbered padlocks, check that unique identifiers (e.g., asset tags, employee IDs) remain legible and intact.
2. Cleaning & Lubrication
- Debris Removal: Use a soft brush or cloth to clean dirt, dust, or industrial residue from the lock body and shackle pivot points. Avoid abrasive tools that may scratch surfaces.
- Corrosion Prevention: Wipe metal components with a non-corrosive, silicone-based lubricant (e.g., spray lubricant) to protect against rust, especially in humid or chemically harsh environments. Never use oil-based lubricants, as they attract debris and may degrade plastic/nylon parts.
- Label Maintenance: Clean safety labels (e.g., hazard warnings, lockout instructions) with a mild, non-abrasive cleaner to ensure legibility; replace fading or damaged labels immediately.
3. Compliance & Regulatory Checks
- Standard Adherence: Confirm that padlocks meet required safety standards (e.g., OSHA for workplace LOTO, ANSI for performance ratings) and are appropriate for the intended hazard (e.g., electrical, mechanical, chemical).
- Expiry Dates: For time-sensitive applications (e.g., disposable or single-use padlocks), replace them before expiration to avoid compromised security.
- Key Management: Audit key control protocols to ensure only authorized personnel have access, and spare keys are stored securely (e.g., in designated lockboxes with access logs).
4. Storage & Environmental Care
- Protective Storage: Store unused padlocks in dry, clean environments away from direct sunlight, extreme temperatures, or corrosive substances (e.g., solvents, salt air). Use sealed containers or anti-corrosion packets for long-term storage.
- Weather Resistance: In outdoor or exposed settings, prioritize padlocks with weatherproof coatings (e.g., stainless steel, powder-coated shackles) and perform frequent inspections to address environmental wear promptly.
5. Replacement & Record-Keeping
- Wear & Tear Thresholds: Replace padlocks if they exhibit:
- Stiff or unreliable locking mechanisms after lubrication.
- Damaged shackles (e.g., stretched, misaligned) that compromise security.
- Faded or missing safety information critical for LOTO compliance.
- Maintenance Logs: Maintain detailed records of inspections, lubrication dates, repairs, and replacements to demonstrate due diligence and facilitate regulatory audits.
6. Employee Training
- Proper inspection and maintenance procedures.
- Recognizing signs of padlock deterioration (e.g., reduced shackle tension, key jamming).
- Adhering to lockout/tagout protocols and reporting issues immediately.
Conclusion

Product Quality Commitment Letter
Unique Key System for Each Employee and Usage of Different Padlocks for Various Scenarios
[Company Address, Contact Information]
April 28, 2025
1. Adherence to Standards & Compliance
2. Stringent Quality Control Protocols
- Supplier Validation: Comprehensive evaluation of vendors to ensure materials and components meet predefined specifications.
- In-Process Inspections: Continuous monitoring of manufacturing stages via advanced testing equipment and methodologies (e.g., statistical process control, non-destructive testing).
- Final Product Testing: Mandatory performance, durability, and safety assessments to validate compliance with design intent and functional requirements.
3. Customer-Centric Excellence
- Feedback Integration: We maintain robust channels for customer input, using insights to refine products and enhance user experience.
- Transparent Communication: Any deviations from quality standards are promptly addressed through clear, proactive communication, ensuring accountability at every touchpoint.
- Post-Sales Support: Our commitment continues with responsive service, including technical assistance, warranty coverage, and product lifecycle management.
4. Continuous Improvement
- Research & Development: Exploring cutting-edge technologies and methodologies to elevate product performance.
- Employee Training: Regular upskilling of our team to foster expertise in quality assurance, lean manufacturing, and risk management.
- Root Cause Analysis (RCA): Systematic investigation of issues to prevent recurrence and optimize processes.
5. Environmental & Social Responsibility
Accountability

Custom Safety Tags
Lockout/Tagout (LOTO) Tags